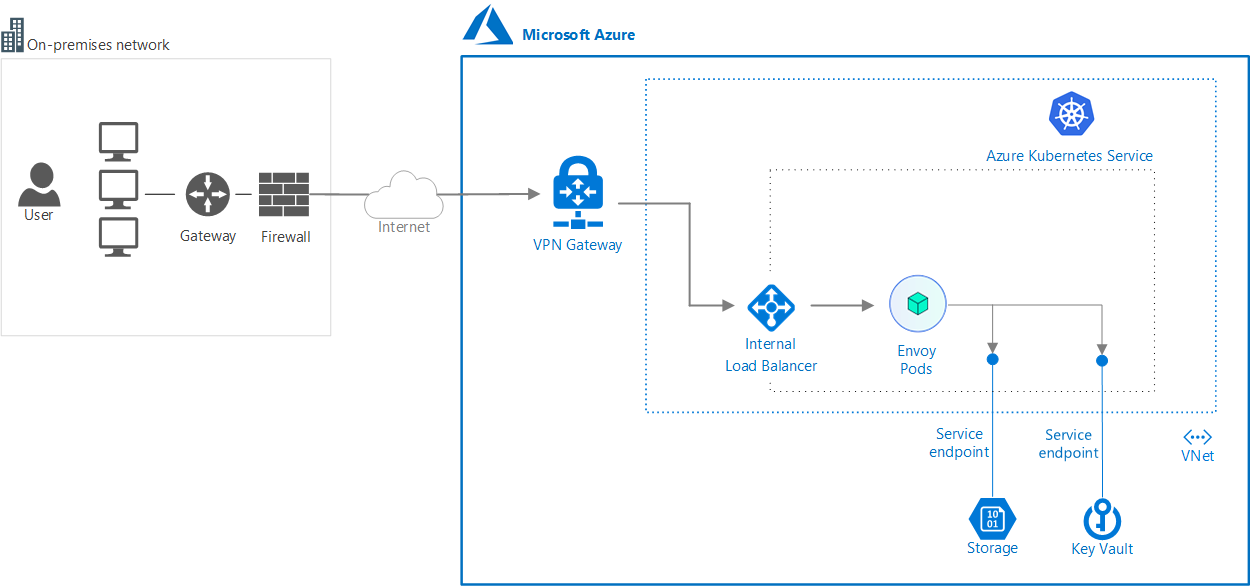
Virtual Network service endpoints allow you to secure some critical Azure services to only specific virtual networks. There is a limitation, though: you can’t use endpoints for traffic from your premises to Azure services.
Right now, if you want to allow traffic from on-premises, you must also allow public IP addresses from your on-premises.
In this article you will find out how to allow your communications to securely go through your VPN by using Envoy as a proxy.
The idea is to reach, via VPN, an Envoy proxy pod located inside an AKS Cluster. Of course, you need to deploy this cluster in one of the VNets allowed to access Azure resources through Service Endpoint.
Here you will find a repository containing a sample Envoy configuration and two console applications you can use for test.